Delights of a Minnesotan Gigabit Switch (part 2, good fans and bad hax)
My charming blue piece of history arrived with two problems:
- Its fans were noisy
- Its management interface was locked and I didn’t know the password
Good Fans
For problem 1, the solution was obvious: new fans. It needs two of these:
The OEM parts only seems to exist in odd places now, but the concept is universal and cheap: 5 Volt 40x40x10mm fans. PCs use 12 Volt versions, you have to be careful to get 5V. And match or go under the watts of the existing item. I bought Noctua NF-A4x10 5V fans, with 3-pin connections. This worked fine, except that the original fans’ power connectors appeared to be wired backwards from the new ones. WTF wat. I checked with a voltmeter and yeah.
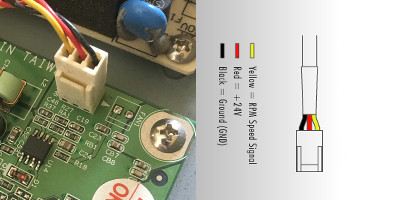
The helpful Austrians at Noctua anticipated this kind of problem, and sent some solderless, insulation displacement connectors and plenty of adaptors and extension cables. This let me fix the wiring without destroying anything actually connected to the fan. The connectors, the transparent orange thingies flopping around below, work great, but only if you squash them COMPLETELY. My fingies, my hands, and even I’m ashamed to say my teeth, were not sufficient to close them and make a good connection - pliers are a must.
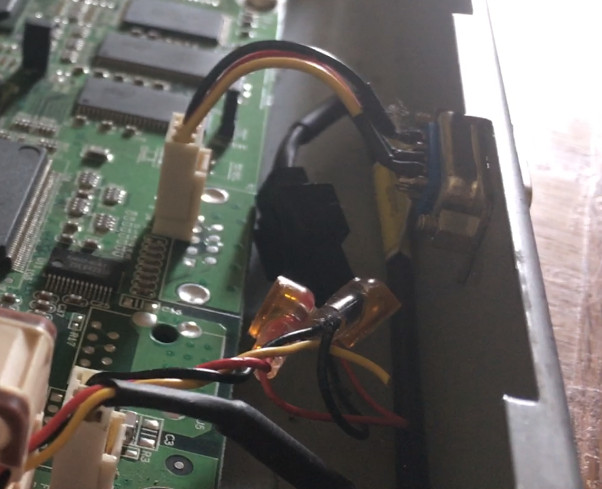
The fans are quiet! One reason they’re quiet is that they’re lower power than the old ones, but with only three Powered Devices attached, I’ve never noticed the switch get hotter than ambient.
A weird thing is that I’m 80% sure the fans blow in opposite directions. The one you can see well in the video is an exhaust fan, but I think the other one blows on the “lee side” of the PoE power supply, so that it isn’t becalmed.
Bad Hax
Anyway, that accomplished, it was time to attempt to gain control. The switch’s model number is Waters Network Systems GSM-2112-POE. Here is its manual. As it arrived, I did not even know its IP address - I tried pinging its factory default, but no dice.
To find what it thought of as its address, I connected to it with an ethernet cable and ran sudo tcpdump -i enp38s0f1 (the latter being the name of my wired ethernet device apparently). This worked, it considered itself 10.216.0.210. I set my laptop up as its neighbor, .209, added a route, and sure enough I could ping it now. Time to telnet!

That’s from their manual - it looks so easy! But the default admin/admin login was not in place. I dejectedly tried passwords like admin, nimda, root, toor, wizard, 12345, qwerty, asdf, zxcv, xyzzy, hunter2, and so on, but alas: nuthin.
I poked around for a telnet password brute-force program, and found Hydra plus a list of the 10k most common passwords. I set it going, but it turned out that the telnet service on the box was not actually reliable enough to brute force very well. Apart from actual failed logins, it would also just disconnect pretty often.
I had noticed that if you fail to login, it will eventually provide you help:
Please keep the serial number and contact the sales representative !
213-034101000022-1
L2 Managed Switch - GEPoEL2-SW12
Login:
This implies that there’s some way to reset the password over the network, maybe over telnet or maybe with a magic packet of some kind, computed from the serial number? Without anything more specific to go on, I didn’t feel like investigating further. I did try actually contacting sales, but Waters Network Systems’ sales staff did not get back to me despite my polite and complimentary e-mail. All the phone numbers I tried from the web site were disconnected. I tried hard in google and found a current office for the company in a town called Hayfield: it does seem to exist still, but I was making progress on other fronts so I never did manage to get in touch.
Inside the case are two jumper switches, and on the outside is a Reset button. I thought maybe it would do a factory reset if you cross your eyes, remove one jumper, hold Reset for 22 seconds, and pray to Saint Dunstan (patron saint of locksmiths)? I tried every combination of the jumpers and the button I could think of, but no joy.
The switch runs its management web site on thttpd 2.0.4, which was released in 1998.
HTTP/1.1 200 OK
Server: thttpd/2.04 10aug98
And sure enough, it has a 1998-style security hole: a buffer overflow when parsing the If-Modified-Since header, discovered by DJB (who has the coolest domain name, cr.yp.to). Unfortunately, I was not able to find a pre-made exploit for this two decade old vulnerability. And in terms of actual development of exploits, I know just nothing at all. Smashing the Stack for Fun and Profit passed me right by…
But there could still be web app vulnerabilities! Command injection! Arbitrary file reads! That would also be right in style for 1-2 decade old software! Even before I logged in, some of the pages would load skeleton versions with no data. But I was having a heck of a time guessing more than a couple page names, and the manual frustratingly did not show the URL bar on the screen caps. One feeble exception:
At this point, I ordered a USB -> db9 serial cable. I hoped that the console port on the back would give me more privileged access.

Spoilers, YES it did! I recommend that you get excited for PART THREE in which I… PWN! THAT! SWITCH!